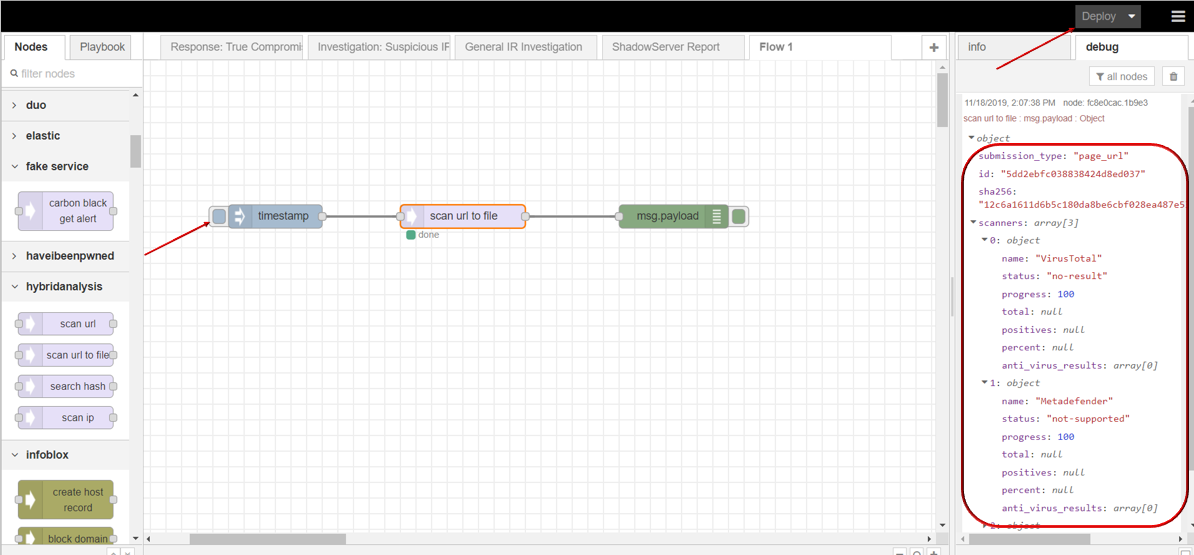
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'https://hybrid-analysis .com/Part-RU/daa8547f1dbc8c994eed3725f3076aaf6c4e298b963fb712e53eb0fa2dc1e789'

Intro to Malware Analysis. What to do when you run into a… | by "CyberGuard: Malware and Vulnerabilities Analysis" | Jan, 2024 | Medium